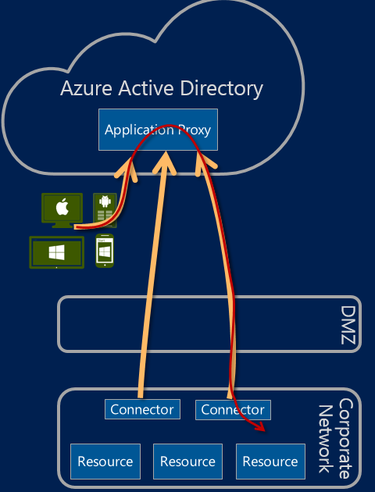
Sophos XG Firewall: Configure AD/LDAP authentication over SSL/TLS due to Microsoft's new recommendation KB-000039329 Feb 8, 2021 3 people found this article helpful. Overview On 10 March 2020, Microsoft recommended moving to LDAP channel binding and LDAP signing to avoid replay attacks on the LDAP communication. You can add existing Active Directory users to XG Firewall. Add an AD server, import groups, and set the primary authentication method. Objectives When you complete this unit, you’ll know how to do the following: Add and configure an Active Directory server on the firewall. Import AD groups using the Import group wizard. To integrate the XG firewall with Azure AD, we need to create a new service called “Azure AD Domain services”. With this integration, administrators can use Azure AD for the following: Captive portal authentication of internal firewall users. Authentication agent for windows, mac, linux.
You need:- A Microsoft Azure subscription.
- Azure Active Directory.
To configure Azure Active Directory synchronization: Assassins creed 4 black flag ultra low mod.
- Set up your Azure applications. To do this follow the instructions in Prerequisites to access the Azure Active Directory reporting API and the instructions in the next two steps.
- In To register an Azure AD application, do as follows:
- Enter a Name.
- Enter https://central.sophos.com in Redirect URI.
- In Get your application’s client secret, do as follows:
- Enter a description and expiry date.
- Make a note of your Client secret and Secret expiration date.
- Make a note of your Application (client) ID and Primary Domain.
- In Sophos Central, in the left-hand pane, select Settings.
- On the Settings page, under Administration, select Azure AD Sync Settings/Status.
- On the Azure Sync Settings/Status page, select Edit.
- In the Edit Azure AD Sync dialog box, enter the following information, which you obtained when you set up your Azure applications:
- Client ID
- Tenant Domain
- Application Key (client secret)
- Application Key Expiration
You do not have to set the expiration date. We recommend that you do enter it so that Sophos Central can send you notifications of when your key is about to expire.
- Select Test Connection to validate the Azure Sync connection.
- Select Save.
- On the next menu, select Sync to import users.
Synchronization starts. This process may take some time.
Follow these instructions to synchronize with Azure Active Directory.
Sophos Xg Firewall Azure Ad
 You need:
You need: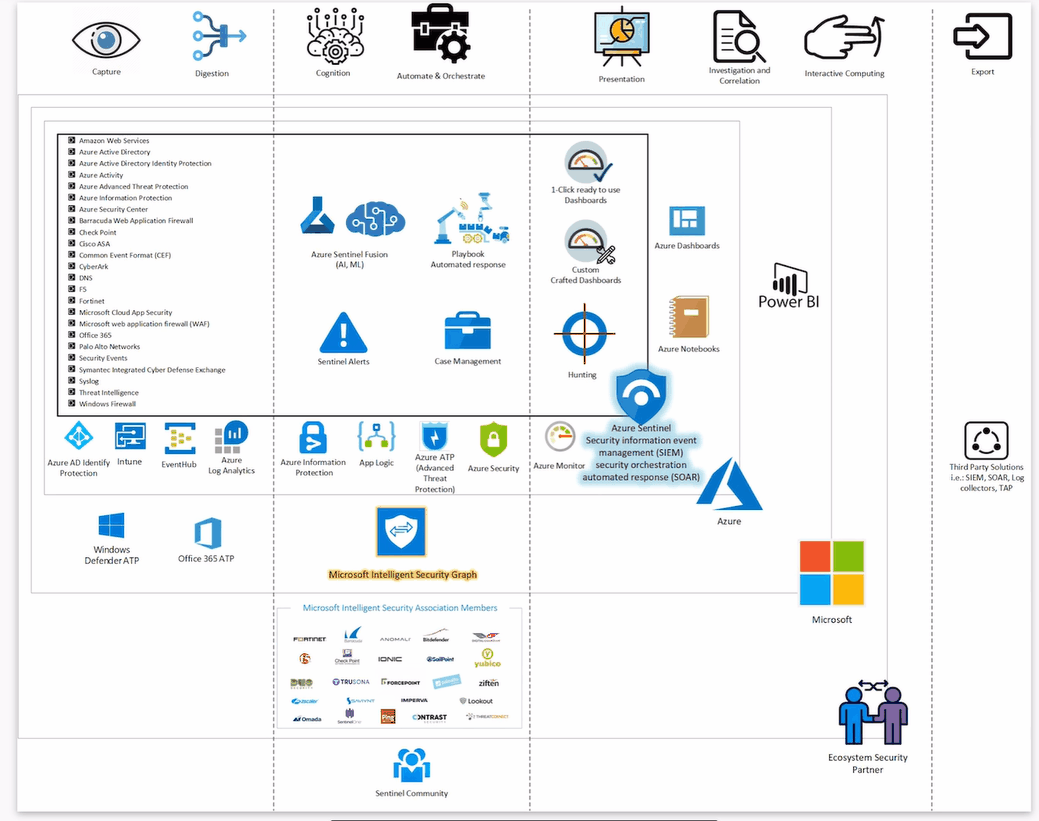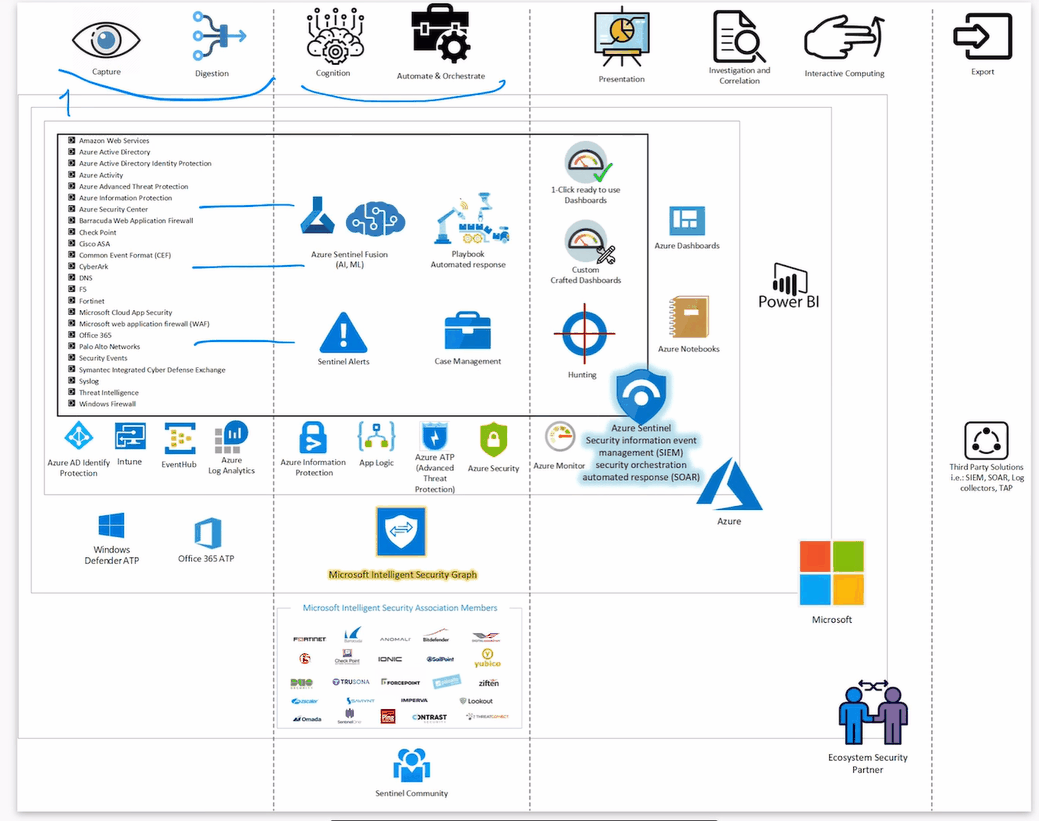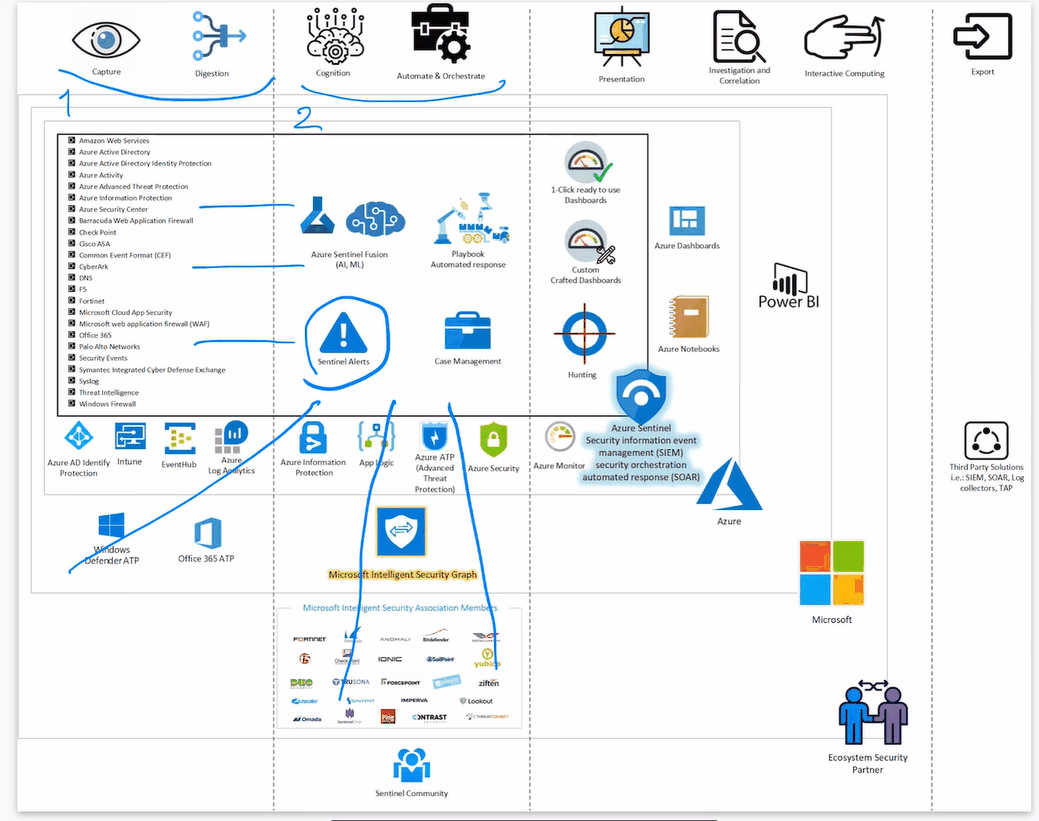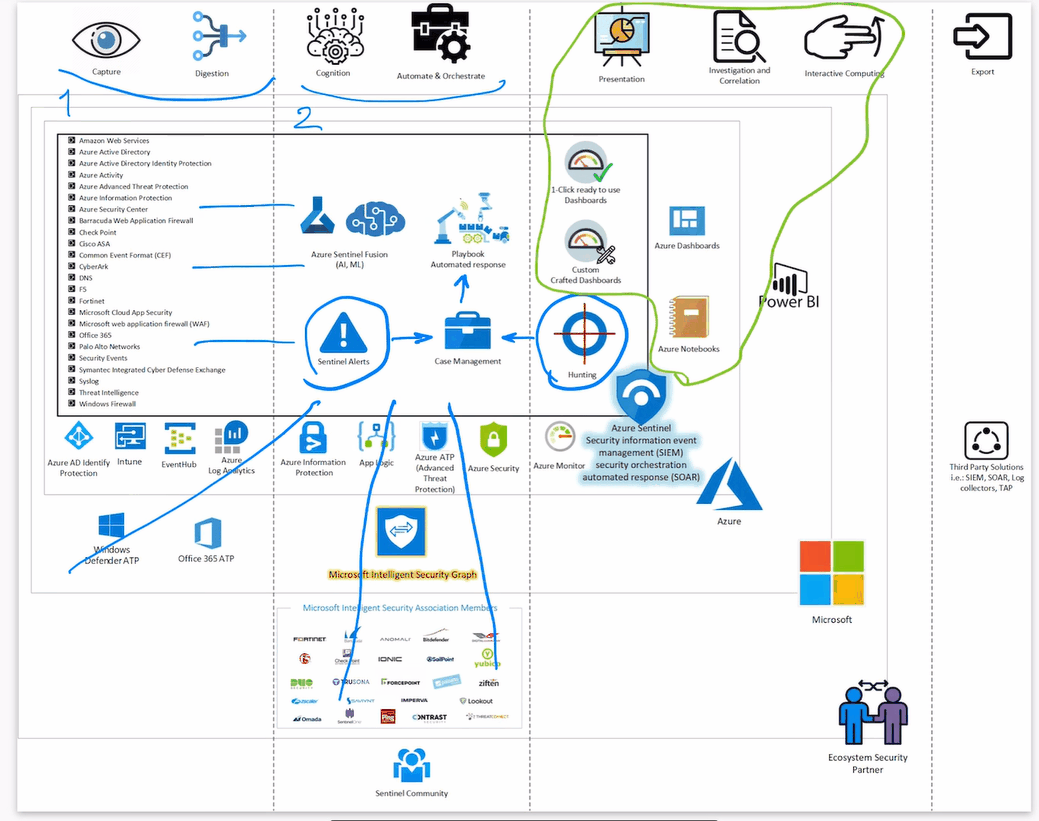
- A Microsoft Azure subscription.
- Azure Active Directory.
To configure Azure Active Directory synchronization:
Sophos Xg Firewall Setup

Sophos Xg Azure Ad Sync
- Set up your Azure applications. To do this follow the instructions in Prerequisites to access the Azure Active Directory reporting API and the instructions in the next two steps.
- In To register an Azure AD application, do as follows:
- Enter a Name.
- Enter https://central.sophos.com in Redirect URI.
- In Get your application’s client secret, do as follows:
- Enter a description and expiry date.
- Make a note of your Client secret and Secret expiration date.
- Make a note of your Application (client) ID and Primary Domain.
- In Sophos Central, in the left-hand pane, select Settings.
- On the Settings page, under Administration, select Azure AD Sync Settings/Status.
- On the Azure Sync Settings/Status page, select Edit.
- In the Edit Azure AD Sync dialog box, enter the following information, which you obtained when you set up your Azure applications:
- Client ID
- Tenant Domain
- Application Key (client secret)
- Application Key Expiration
You do not have to set the expiration date. We recommend that you do enter it so that Sophos Central can send you notifications of when your key is about to expire.
- Select Test Connection to validate the Azure Sync connection.
- Select Save.
- On the next menu, select Sync to import users.
Synchronization starts. This process may take some time.

